Cyber Threats
Cyber Threats
Malware is the collective name for a number of malicious software variants, including viruses, ransomware and spyware. Shorthand for malicious software, malware typically consists of code developed by cyberattackers, designed to cause extensive damage to data and systems or to gain unauthorized access to a network. Malware is typically delivered in the form of a link or file over email and requires the user to click on the link or open the file to execute the malware.
Malware has actually been a threat to individuals and organizations since the early 1970s when the Creeper virus first appeared. Since then, the world has been under attack from hundreds of thousands of different malware variants, all with the intent of causing the most disruption and damage as possible.
Malware :

Malware, short for malicious software, is a blanket term for
viruses, worms, trojans and other harmful computer programs hackers use
to wreak destruction and gain access to sensitive information.
Viruses :

Malicious cod ethat runs on machine without the user's knowledge and infects the computer when executed.
Virus require a user action in order to reproduce and spread.
> Boot sector : -
Boot sector virus are stored in the first sector of a hard drive and are loaded into the memory upon boot up.
>Macro :-
Virus embeded into a document and is executed when the document is opened by the user.
>Program :-
Program virus infect an executable or applcation
>Multipartite :-
Virus that combines boot and program viruses to first attach itself to the boot sector and system files before attacking other files on the computer.
>Polymorphic :-
Advanced version of an encrypted virus that changes itself every time it is executed by altering the decryption module to avoid detection.
>Matamorphic :-
Virus that is able to rewrite itself entirely before it attempts to infect a file.
>Armored :-
Armored viruses have a layer of protection to confuse a program or person analysing it.
>Hoax :-
A computer virus hoax is a message warning the recipients of a non-existent computer virus threat.
Worm :
A worm virus is a malicious, self-replicating program that can spread throughout a network without human assistance.
Rensomware :
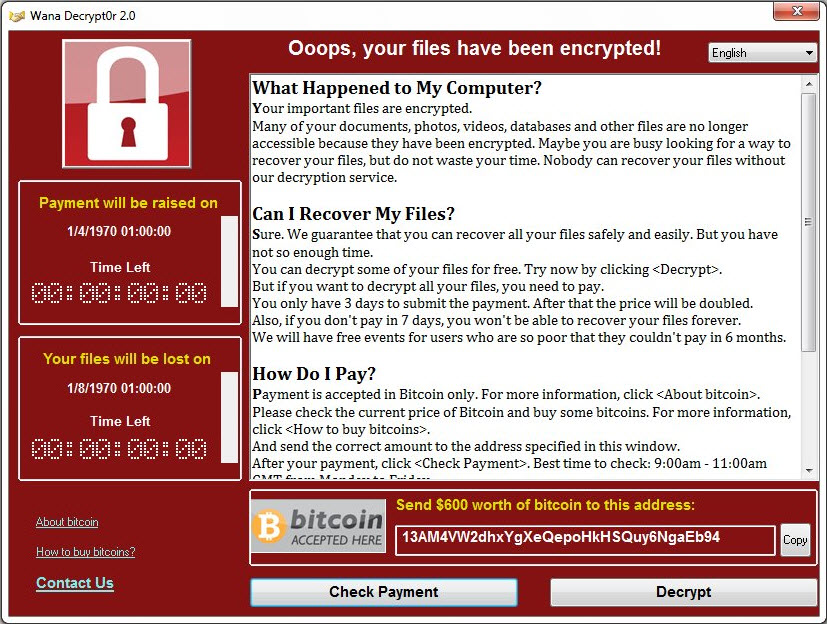
Ransomware is a type of malware from cryptovirology that threatens to publish the victim's data or perpetually block access to it unless a ransom is paid.
Trojans :
A Trojan horse (or simply trojan) is any malware which misleads users of its true intent.
Spyware :

Spyware is a kind of malware that secretly gathers information about a person or organization and relays this data to other parties.
Adware :

Adware is unwanted software designed to throw advertisements up on your screen, most often within a web browser.
Rootkit :

A rootkit is a clandestine computer program designed to provide continued privileged access to a computer while actively hiding its presence.
Spam :

Spam is digital junk mail: unsolicited communications sent in bulk over the internet or through any electronic messaging system.
How to Protect Against Malware
Now that you understand a little more about malware and the different flavors it comes in, let's talk about protection. There are actually two areas to consider where protection is concerned: protective tools and user vigilance. The first is often the easiest to implement, simply because you can often set and forget best-in-class protective software that manages and updates itself. Users, on the other hand, can be prone to temptation ("check out this cool website!") or easily led by other emotions such as fear ("install this antivirus software immediately"). Education is key to ensure users are aware of the risk of malware and what they can do to prevent an attack.
With good user policies in place and the right anti-malware solutions constantly monitoring the network, email, web requests and other activities that could put your organization at risk, malware stands less of a chance of delivering its payload. Forcepoint's Advanced Malware Detection offers best-in-class malware protection across multiple channels and is unmatched in security efficacy.
Malware security protection provides that second vital layer of protection for your computer or network. A robust antivirus software package is the primary component of technological defenses that every personal and business computer system should have.
Well-designed antivirus protection has several characteristics. It checks any newly downloaded program to ensure that it is malware-free. It periodically scans the computer to detect and defeat any malware that might have slipped through. It is regularly updated to recognize the latest threats.
Good antivirus protection can also recognize — and warn against — even previously unknown malware threats, based on technical features (such as attempting to "hide" on a computer) that are characteristic of malware. In addition, robust antivirus software detects and warns against suspicious websites, especially those that may be designed for "phishing" (a technique that tricks users into entering passwords or account numbers).
Finally, malware protection needs to be usable. Effective antivirus software must be simple to download and install, so you don't need to be a Ph.D. in computer science in order to use it. Look for antivirus software solutions that have the characteristics outlined above — and follow through by installing it.
Robust malware protection specifically guards your finances. These tools safeguard your account information, and can also provide password-management tools so that frustration over forgotten passwords does not lead you to skip over this essential component of protection.
No protection is absolute. But a combination of personal awareness and well-designed protective tools will make your computer as safe as it can be.
Comments
Post a Comment